For this discussion I am going to dive into more DAI and the additional features that It has. The two additional features that can be optionally added on top of DAI are “optional checks” and “rate limiting.” DAI optional checks are optional features that can be added after the IP to MAC mapping has been validated. The options include verifying IP address, sender MAC, Destination MAC, or all of them together. It is usually written in this type of command
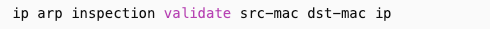
We will cover this command in more detail later. When the source MAC optional check is chosen, and an ARP message is sent onto the network, DAI intercepts the frame per usual, does the typical IP to MAC verification from the DHCP binding table or static ARP ACL but now it does one more thing. After the frame passes the first round of IP to MAC validation, it then does another verification check where it inspects the source MAC of the ethernet frame and the sender MAC field of the ARP payload. If you don’t understand this, I did a deep dive with visuals on what this looks like here (https://networkingnotebook.com/?p=154). If it matches, the ARP frame will be allowed to traverse the network, if it does not match, the ethernet frame is considered not valid and is dropped.
Now what about if the Network Engineer chooses destination MAC? Well the same thing happens, it will go through the usual IP to MAC verification against the DHCP binding table or ARP ACL first, and then the destination MAC in the Ethernet frame will be verified against the target MAC in the ARP payload. If it matches, the frame will be allowed to traverse the network, and if it doesn’t it will not be allowed to traverse the network as the frame will be deemed invalid.
Now what if the engineer chooses IP, well then it will do the usual IP to MAC validation against DHCP binding table or ARP ACL, but also check to see if the IP does not equal to any suspicious IP address. It checks for IP addresses that are out of place such as an IP equal to 0.0.0.0, 255.255.255.255, or any multicast address that shouldn’t even be in the ARP payload.
Now when this command is being put into place, you must be very careful on what you are trying to do. Unlike an ACL, where you can have additional separate entries and the first entries will not be impacted, this is the opposite. If you want source MAC optional check you will type:

If you then decide you want both IP and MAC to be checked, you must write it like this:

If you write it like

the later command which is source IP will take precedence and completely wipe out any commands for optional checks before it. So the key take away is that there is only ONE final command. You can include just source MAC, destination MAC, IP address, any two, or all three. But if you chose two or all three, they must all be in ONE single command.
Now let’s talk about rate limiting, what about DOS attacks? We’re probably both thinking the same thing, what is stopping an attacker who does not get through because of DAI and just completely floods the switch with frames wasting bandwidth, CPU and overwhelming the switch. Well that’s what DAI rate limiting is for! This is an additional feature that limits the amount of ARP packets that a specific port can receive within a second. The default amount is usually 15 packets per second(not all the time, it is platform-dependent) but it can be configured to any amount the Network Engineer chooses. Say an attacker floods ARP packets at 18 packets per second, when the port detects that more packets are sent than the allowed amount, the port will be automatically shut down until further notice if it is configured to errdisable mode.It can either be automatically re-enabled or manually enabled whichever the engineer prefers. This will stop DOS attacks from overwhelming the switch and provides great security especially for a Layer 2 feature, which has limited visibility compared to higher layers. These are very important features of DAI and I hope you clearly understand what DAI is about now. If you missed the last post about DAI and how it works without these additional features here is the link(https://networkingnotebook.com/?p=220)!
Leave a Reply