Today I am going to talk about TCP (Transmission Control Protocol), and all of its features that it provides layer 4. TCP is a transport layer protocol that is widely used for the bulk of the applications used today such as FTP, SMTP, POP3, Telnet, SSH, HTTP, and HTTPS.
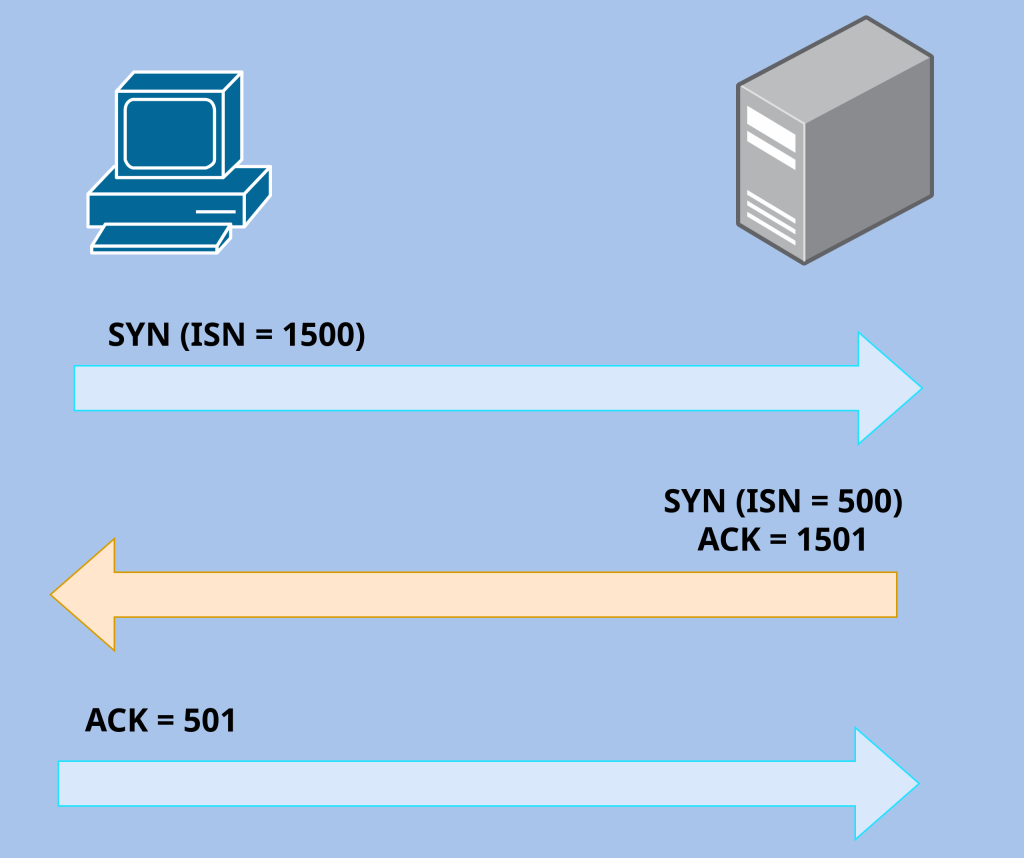
Connection-Orientated- TCP is a transport layer protocol known for its reliability due to it being a “connection-orientated” protocol. By “connection-orientated” I mean that a connection has been fully established before data begins transferring. Before data can begin transferring a client and a server go through a process called a “3 way handshake.” This process is used to synchronize sequence numbers, establish bidirectional communication, and verify both endpoints are ready to exchange data. The client usually starts the connection with a “SYN” packet. This SYN segment has key information inside the header called an ISN (Initial Sequence Number). This number is a random number generated to determine the start of the first byte to be delivered. Application data are split into multiple segments based on the Maximum Segment Size. The client and server will keep track of these segments through sequence numbers and acknowledgements.
Sequence Numbers- The sequence number sent will be representative of the first byte of the segment, and will be incremented according to the first byte being sent of the segment. This sequence number will essentially be the identifier for segments. Sequence numbers play a crucial role in TCPs reliability as it can be used to detect lost or missing segments, detect duplicate segments, and allow the receiver to reorder any segments that arrived out of order. The reason why the first sequence number is a random sequence number is to prevent malicious TCP attacks where the attacker will try to guess the sequence number. An example of how sequence numbers are used is the client initiates a session with a server and sends a random sequence number (ISN) of 1500, and for this sequence number it does not account for any data payload. Once the session is established, then the first byte of data that will be sent will be sequence number 1501, and if it sends 499 bytes then the next sequence number will be 2000. If the bytes sent is 499 bytes again then the next sequence number will be 2500 and so on.
Three-Way Handshake- After the first SYN is sent with the ISN of the client, the server then sends a SYN-ACK. This is a combination of both a SYN and an ACK. So the SYN being the servers own ISN which is completely random and not related to the clients number, then the ACK is to acknowledge the clients SYN putting the value of the clients ISN + 1.
Once the client receives the SYN-ACK flags in the TCP segment, it will send a final ACK flag with the value of the server’s ISN + 1. After this ACK is received, the connection has been established and data is ready to be transferred.
The rest of the exchanges will just be data being sent and since the connection is most likely full-duplex both sides can send data at the same time. Once the connection is established, TCP segments will be back and forth with the sequence numbers in the headers and ACK flags with the value of the next expected byte.
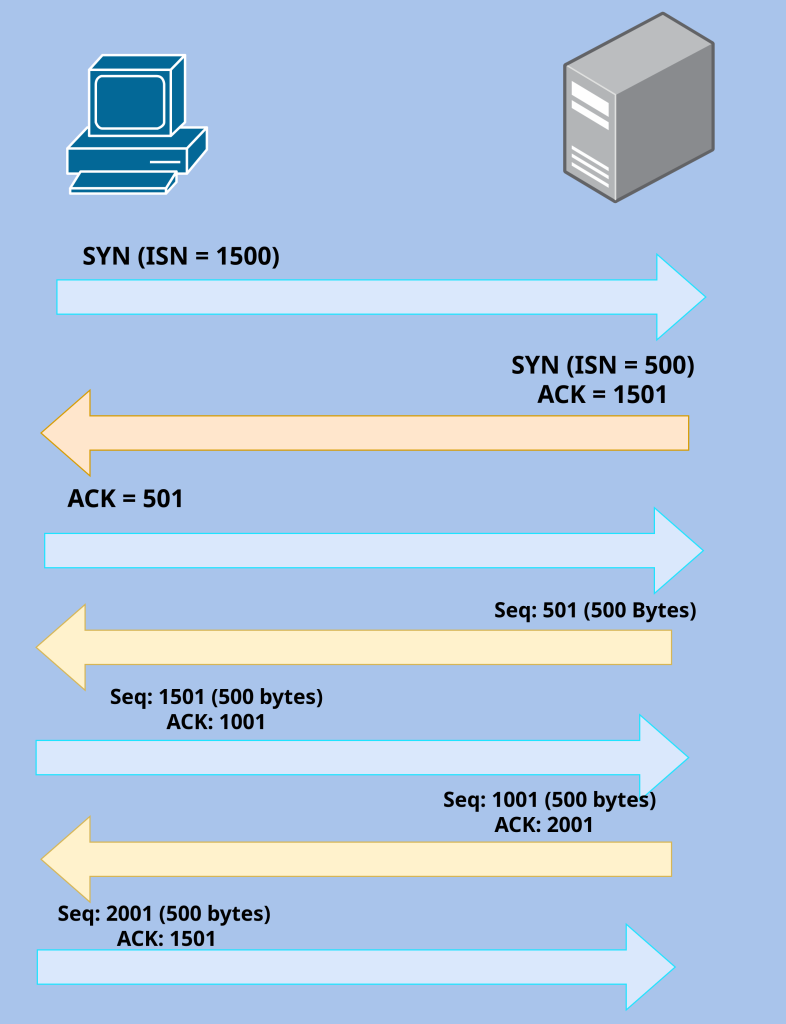
Cumulative Acknowledgement- In TCP, there is something called “Cumulative Acknowledgement.” Every segment must be acknowledged. Since every segment contains its own segment number, cumulative acknowledgement prompts the receiver of the segment to send an ACK that contains the value of the next expected byte that is to be received. So if a client sends a segment to a server with a sequence number of 500 that is 500 bytes large, the server will acknowledge this number by sending a TCP segment with an ACK flag with the value of 1000. This indicates that the server received bytes 500 to 999, and is expecting a TCP segment with a sequence number of 1000. This allows every single segment to be acknowledged up to the byte.
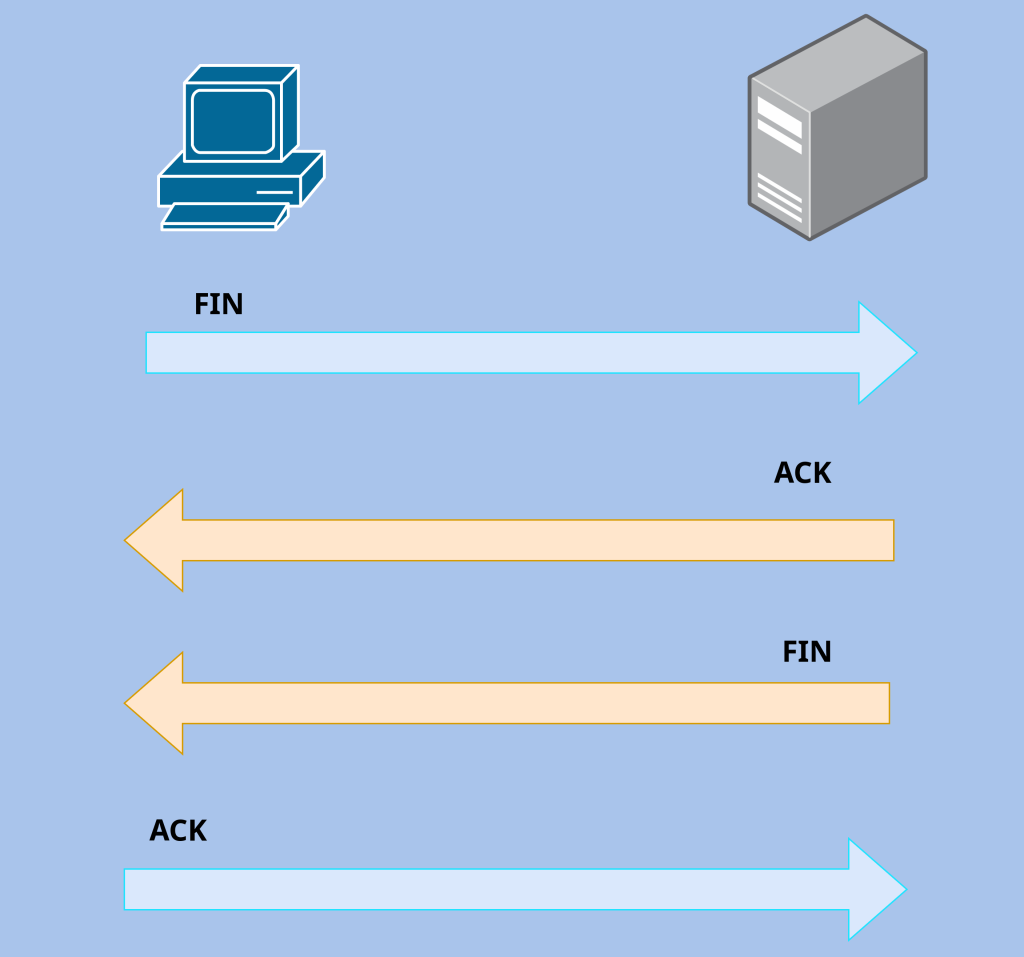
Four-Way Handshake- TCP also closes the connection gracefully. When one side is done transferring data it sends a TCP segment with the FIN flag set. When the server receives the segment with the FIN flag, it will send back a segment with an ACK flag. This ACK will close one half of the communication. Since it is full duplex, both sides need to terminate the connection independently. During this half-closed state, the server can finish sending whatever data it needs to send and once it’s finished it will send a TCP segment with a FIN flag set. When the client receives that and sends back a segment with an ACK flag, the connection will finally be closed and gracefully.
Leave a Reply